Last Updated on February 17, 2026 by Narendra Sahoo
When we talk about HIPAA compliance for dental offices, we’re not talking about theory or paperwork. We’re talking about patient privacy, regulatory exposure, and whether a practice can keep operating when something goes wrong.
HIPAA is no longer a “back-office” concern—it’s a core part of running a modern dental practice. Dental offices process and store large volumes of protected health information (PHI) every day, from X-rays and treatment plans to insurance data and billing records. That makes them high-value targets for attackers and fully accountable under HIPAA regulations.
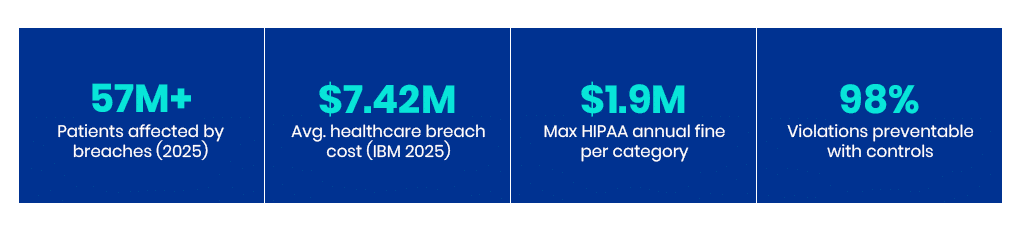
In 2024, the HHS OCR breach portal reported tens of millions of patient records were exposed via hundreds of breaches. Sprinto reported a long-term upward trend: between 2009 and 2024: 6,759 healthcare data breaches affected 846,962,011 people. As of late 2025, large healthcare breaches have affected nearly 57 million people. Healthcare breaches cost more than in other industries: IBM reported that (IBM’s 2025 Cost of a Data Breach Report) the average healthcare breach cost was $7.42 million while in the US it averaged $10.22 million. Phone and email attacks are common entry points, with cyberattacks impacting 93% of organisations in 2025.
Is Your Dental Practice HIPAA Ready?
Take our free 5-minute HIPAA Readiness Assessment. Get an instant gap report and a prioritised action plan tailored to your practice size.
👉 Start Your Free HIPAA Assessment →
1️⃣ Does HIPAA Apply to Dental Offices?
Yes — HIPAA applies to virtually every dental office in the United States. A dental practice becomes a ‘covered entity’ the moment it transmits health information electronically — which includes submitting a single insurance claim via email or a third-party billing service. Even if your practice has never submitted a claim electronically, you may still be bound by HIPAA contractually through a participating provider agreement with an insurer. Beyond the covered entity question, a solo dentist is legally required to designate themselves as the HIPAA Privacy Officer and HIPAA Security Officer — or appoint a qualified individual to fill both roles. Failing to do so is itself a documentable violation, regardless of whether a breach has occurred.
HIPAA for dentists goes far beyond chairside care. It requires structured policies, workforce training, and documented safeguards that govern who can access records, how systems are used, and how patient data is protected every day.
A single-location dental office is held to the same HIPAA Security and Privacy Rule standards as a multi-site healthcare provider. Performing an annual HIPAA risk assessment is the only way to identify ‘hidden’ vulnerabilities in how your team handles imaging and billing data. Meeting HIPAA dental requirements means aligning privacy, security, and breach response controls with how data is used across systems, staff, and vendors—not just how it’s described in a policy document. Cyber incidents often involve third parties: Breaches often spread through business partners or shared services — a pattern in many healthcare breaches listed by the OCR portal.
What HIPAA Covers in Your Office:
- Patient Data: Records, charts, and X-rays (digital and paper).
- Systems: Practice management and scheduling platforms.
- Financials: Insurance and billing data.
- Communications: Emails, backups, and lab integrations.
VISTA InfoSec Case Study: Eliminating Audit Gaps Through Individual Access Controls
Challenge: A multi-operatory dental practice relied on shared workstation logins across the front desk and clinical team. 60% of audit failures traced directly to the inability to attribute record access to a specific user. OCR’s first request in any investigation is an access log showing which user accessed which record and when. With shared logins, that log was blank. Solution: VISTA InfoSec implemented unique user IDs, Role-Based Access Control (RBAC), and automated audit logging — aligned to HIPAA Technical Safeguard requirements under §164.312(a)(1). Access tiers were mapped to clinical vs. administrative roles, ensuring staff only saw the records required for their function. Result: Access-related audit findings dropped by 45% in a single review cycle. The practice now produces a full, attributable access trail on demand — the single most important document during an OCR investigation. → See how VISTA InfoSec’s HIPAA consulting programme closes access control gaps →
2️⃣ What Is Considered PHI in Dental Practice?
In a dental office, Protected Health Information (PHI) is broader than many practices realize. Under HIPAA, PHI includes any information that can identify a patient and relate to their health, treatment, or payment. See the full HHS definition of PHI for the complete regulatory definition.
Common examples include:
- Dental charts, clinical notes, and treatment plans.
- X-rays, intraoral images, and scans.
- Billing records and appointment schedules.
- Patient contact details and insurance IDs.
Under HIPAA, PHI is specifically defined by 18 identifiers. If any of these data points accompany health or payment information, the entire record becomes PHI:
- Names, geographic data smaller than a state, dates (except year) directly related to a patient
- Phone numbers, fax numbers, email addresses, Social Security numbers
- Medical record numbers, health plan beneficiary numbers, account numbers
- Certificate/license numbers, vehicle identifiers, device identifiers
- Web URLs, IP addresses, biometric identifiers (fingerprints, voice prints)
- Full-face photographs, any other unique identifying number or code
Important Note: PHI is not limited to electronic systems. Paper charts, printed schedules, and physical X-rays are all in scope. HIPAA applies equally to information stored digitally or on paper.
VISTA InfoSec Case Study: Securing the Front Desk Against Physical PHI Exposure
Challenge: Physical PHI at the front desk — visible screens and unsecured charts — accounted for 40% of one practice’s total HIPAA exposure. Because healthcare breaches take an average of 279 days to contain, immediate physical containment is vital. The practice had no documented disposal protocol and no screen privacy controls. Solution: VISTA InfoSec introduced privacy screens on all reception-facing monitors, locked lateral filing for paper charts, and a documented disposal protocol requiring cross-cut shredding. Staff acknowledgement was logged to create an auditable training record. Result: Physical safeguard findings were eliminated in over one-third of recurring compliance review areas. The practice’s first line of defence was hardened without disrupting front-desk workflows. → Get a free on-site physical safeguard assessment from VISTA InfoSec →
3️⃣ Core HIPAA Rules for Dental Offices
HIPAA is structured around three core pillars. Understanding these is essential for building a defensible program:
The Privacy Rule governs how Protected Health Information (PHI) may be used and disclosed. It limits access to only what is necessary for treatment, payment, and operations, and grants patients specific rights over their information, including access and amendment. For dental offices, this affects everything from front-desk workflows to how records are shared with insurers and labs.
The Security Rule focuses specifically on electronic PHI (ePHI). It requires dental practices to implement administrative, physical, and technical safeguards to protect patient data. These controls must be reasonable and appropriate for the size, complexity, and technology used by the practice, but they must still be documented and enforced.
The Breach Notification Rule defines what happens when safeguards fail. If unsecured PHI is compromised, dental offices are required to notify affected patients, regulators, and in some cases the media, within strict timelines.
This is where a practical dental office HIPAA checklist matters. It gives practices a repeatable way to assess risk, secure patient data, and produce defensible evidence during audits or investigations.
VISTA InfoSec Case Study: Neutralising Third-Party Risk via Vendor Governance
Challenge: Unregulated vendors are primary vectors for data breaches. VISTA InfoSec discovered a billing vendor handling 70% of a practice’s patient records without a valid Business Associate Agreement (BAA) in place. The vendor had unrestricted network access and no documented security obligations. Solution: VISTA InfoSec formalised BAAs with all applicable third parties, introduced vendor-specific access segmentation, and established a contract review calendar to prevent future lapses. Vendor onboarding now includes a mandatory security questionnaire. Result: Third-party risk exposure was reduced by 50%. The practice remained protected even when data left their internal network, and the BAA registry became a core exhibit in subsequent compliance reviews. → Learn how VISTA InfoSec secures your vendor and BAA governance programme →
4️⃣ HIPAA Security Safeguards
Most dental offices think of HIPAA safeguards as a checklist. They function more like a three-legged stool. Remove one leg, and the entire program collapses under scrutiny.
Administrative Strategy & Planning
The administrative strategy is the control layer. Written policies, risk assessments, and incident response plans define how the office is supposed to operate. Appointing a HIPAA Compliance Officer isn’t a formality—it creates a clear owner for decisions, enforcement, and evidence when regulators ask, “Who is responsible?”
Securing the Physical Environment
Physical safeguards are the exposure layer. Even the best policies fail if charts are visible at the front desk, or laptops can walk out the door. Physical controls limit who can physically touch, view, or remove PHI-bearing devices and records. This is where many “low-tech” violations originate.
Cybersecurity & Technical Controls
Technical safeguards are the enforcement layer. Unique user accounts, encryption, audit logs, and MFA turn intent into enforcement. They ensure access is traceable, misuse is detectable, and ransomware attacks are stopped before they spread laterally through shared credentials. Modern cybersecurity for dental practices must include multi-factor authentication (MFA) to defend against the rising tide of ransomware targeting healthcare providers. Learn more from CISA’s healthcare cybersecurity guidance.
Together, these administrative, physical, and technical safeguards ensure electronic PHI is protected from external threats as well as internal misuse within the dental office.
5️⃣ Why Dental Offices Are a Specific Ransomware Target
Dental practices are not attacked at random. Threat actors select them deliberately, and for specific operational reasons that differ from general small business targets.
Most dental offices run legacy Picture Archiving and Communication Systems (PACS) for X-ray and image storage. These systems were designed for clinical interoperability, not security — many are internet-connected, run unpatched operating systems, and lack basic encryption controls. A single compromised PACS server can expose years of patient imaging data in one event.
The combination of high-value data (PHI with insurance identifiers, SSNs, and financial records), legacy infrastructure, and typically small IT teams with limited incident response capability creates exactly the profile ransomware operators look for: valuable data, weak defences, and a practice owner under regulatory pressure who is more likely to pay quietly than report to law enforcement.
VISTA Insight: In our experience working with dental practices post-incident, the gap between when a threat actor first accessed the network and when the practice discovered the intrusion ranged from six weeks to over four months. By the time ransomware deployed, the attacker had already catalogued the environment, exfiltrated PHI, and identified backup locations. Early detection controls — not just endpoint protection — are what break this cycle.
VISTA InfoSec Case Study: Accelerating HIPAA Inquiry Resolution Post-Phishing
Challenge: In 2025, a dental entity faced a formal HIPAA inquiry following a phishing incident that compromised staff email credentials. The practice had limited documentation of its safeguards, no structured evidence repository, and no prior experience managing an OCR investigation timeline. Solution: VISTA InfoSec implemented a structured evidence approach that anticipated regulatory documentation requirements. This included mapping each HIPAA safeguard to corresponding evidence artefacts, preparing a chronological incident narrative, and pre-emptively addressing known OCR audit request categories. Result: Follow-up requests from investigators were reduced by nearly two-thirds. The total inquiry timeline was shortened by weeks, significantly lowering the risk of escalation to formal enforcement action or financial penalty. Facing an active OCR inquiry? Contact VISTA InfoSec’s incident response team now →
6️⃣ Common HIPAA Violations in Dental Offices
When regulators investigate dental HIPAA violations, they rarely uncover advanced cyberattacks. Most findings trace back to everyday operational shortcuts that quietly break accountability.
Internal Risks: Access & Documentation
Shared Accounts: Shared logins erase accountability — and OCR knows exactly what to look for. When investigators arrive, one of their first requests is an access log showing which user accessed which record and when. If your practice uses a shared login, there is no log — just a blank where evidence should be. This is precisely the scenario that cost Elite Dental Associates in Dallas a $10,000 OCR settlement in 2019: impermissible disclosure of patient ePHI stemming from uncontrolled staff access. See the OCR enforcement database for the full case record.
Improper Disposal: HIPAA treats paper and digital records equally. In 2016, an Illinois dental practice entered a corrective action plan after patient X-rays were found in an unsecured recycling bin. The OCR resolution agreement required a full risk analysis, revised disposal policies, and two years of monitoring.
Lack of Training: OCR’s investigation checklist always includes a training records request. If you cannot produce documentation showing every workforce member received HIPAA training upon hire and annually thereafter, the absence is treated as a safeguard failure — even if no breach occurred. See HHS HIPAA Training Guidance for content requirements.
External Risks: The “Lab” Exception
Third-party risk is an increasing source of violations. Billing companies and IT providers must have a signed Business Associate Agreement (BAA).
Important Legal Distinction: Under HHS OCR guidance, dental labs are classified as “Healthcare Providers,” not “Business Associates.” You do NOT need a BAA to share PHI with a dental lab for patient treatment purposes. This is one of the most misunderstood rules in dental compliance.
→ Read the official HHS guidance on Business Associates →
| Important Legal Distinction: Under HIPAA guidance confirmed by the OCR, dental labs are classified as “Healthcare Providers,” not “Business Associates.” You do NOT need a BAA to share PHI with a dental lab for patient treatment purposes. HIPAA allows providers such as dental labs to exchange data for treatment without a BAA. This is one of the most misunderstood rules in dental compliance — and getting it wrong in either direction creates unnecessary liability. |
7️⃣ HIPAA Violation Penalties: What Dental Offices Face
OCR enforces HIPAA through a four-tier civil monetary penalty structure. See the full HHS HIPAA Enforcement Rule for the authoritative penalty framework.
| Violation Tier | Description | Per Violation | Annual Cap |
| Tier 1 – No Knowledge | Violation the entity was unaware of and couldn’t have avoided | $100 – $50,000 | $25,000 |
| Tier 2 – Reasonable Cause | Violation due to reasonable cause but not wilful neglect | $1,000 – $50,000 | $100,000 |
| Tier 3 – Wilful Neglect (Corrected) | Wilful neglect corrected within 30 days | $10,000 – $50,000 | $250,000 |
| Tier 4 – Wilful Neglect (Uncorrected) | Wilful neglect not corrected within 30 days | $50,000 | $1,900,000 |
Real Dental OCR Enforcement Cases:
2019 — Elite Dental Associates (Dallas, TX): $10,000 settlement after responding to a patient’s negative review by disclosing treatment details and insurance information on a public platform. View OCR enforcement record
2016 — Lincare Holdings / Dental Sector Parallel: A $239,800 settlement arising from an employee’s removal of patient records from the practice premises — records left in a car and later stolen. Physical safeguard failures carry the same enforcement weight as digital ones.
Key principle: OCR does not require a large-scale breach to open an enforcement action. A single patient complaint, a publicly visible PHI disclosure, or a routine compliance audit can all trigger investigation. The practices that settle quickly and cheaply are the ones with documentation. Those without documentation face extended investigations and escalating corrective action plans.
Could Your Practice Afford a $1.9M Fine?
VISTA InfoSec’s HIPAA Gap Assessment identifies which penalty tier your current compliance posture puts you in — and what it takes to move to Tier 1 or 2.
👉 Get Your Free HIPAA Gap Assessment from VISTA InfoSec →
8️⃣ How to Conduct a HIPAA Risk Assessment for a Dental Practice
The HIPAA Security Rule §164.308(a)(1) requires every covered entity to conduct an accurate and thorough risk analysis of potential risks to ePHI. For dental offices, this means a systematic, documented process.
Step 1 — Identify All ePHI Locations
Map every location where electronic PHI exists: practice management software (Dentrix, Eaglesoft, Open Dental), X-ray and imaging servers (PACS), cloud storage services, email platforms, staff laptops, tablets, mobile phones used for patient communications, and any third-party portals accessed by billing or insurance staff. Include data in transit — ePHI sent via email referrals or lab integrations is as much in scope as data at rest on a server.
Step 2 — Identify Threats and Vulnerabilities
For each ePHI location, identify realistic threats: ransomware targeting unpatched software, phishing targeting staff email accounts, physical theft of unencrypted laptops, unauthorised access via shared credentials, and inadvertent disclosure through misconfigured cloud storage. Vulnerabilities are the conditions that make threats possible: lack of MFA, absent encryption, no audit logging, infrequent software patching.
Step 3 — Assess Current Controls
Document what safeguards are currently in place against each threat. Assign a likelihood score (high, medium, low) and an impact score (high, medium, low) to each risk. Risk = likelihood × impact. This produces a prioritised risk register — the core deliverable OCR expects to see during an audit.
Step 4 — Implement and Document Remediation
For each high-priority risk, document the remediation action, the person responsible, and the completion date. OCR does not expect dental offices to achieve zero risk. It expects evidence of a systematic, ongoing process to identify risk and take reasonable steps to reduce it. Documented, incomplete remediation is better than undocumented perfect compliance.
Step 5 — Review Annually and After Operational Changes
The risk assessment is not a one-time exercise. HIPAA requires it to be reviewed whenever environmental or operational changes affect ePHI — when a new practice management system is implemented, when a new vendor is onboarded, when staff expand to remote work, or following a security incident. Document the review date and who conducted it.
9️⃣ HIPAA-Compliant Communications for Dental Offices
One of the most frequent compliance questions from dental office managers involves the tools used for daily communications: email, fax, SMS appointment reminders, and referral transmissions. The short answer is that the communication channel does not determine compliance — the safeguards applied to that channel do.
Standard email platforms — Gmail, Outlook, Yahoo — are not HIPAA-compliant by default. To use email for ePHI, the provider must sign a Business Associate Agreement with your practice and must offer end-to-end encryption. Google Workspace and Microsoft 365 both offer HIPAA-compliant configurations with signed BAAs, but the default consumer versions do not qualify. Sending an unencrypted email containing patient PHI to a referral dentist or lab is a violation, regardless of intent.
SMS & Patient Reminders
Appointment reminder texts are permitted under HIPAA as long as the minimum necessary standard is applied. A reminder stating “you have an appointment tomorrow at 2pm” is generally acceptable. A message including the patient’s name alongside their specific treatment type or diagnosis would be PHI — and requires the patient’s explicit acknowledgement of the risk of text communication. Use a HIPAA-compliant patient communication platform (examples include Klara, Weave, or NexHealth) rather than standard SMS for any message combining identity with clinical content.
Fax
Traditional fax remains HIPAA-compliant as long as the receiving fax number is verified before transmission and a HIPAA cover sheet is used. Internet fax services (eFax, MyFax, RingCentral Fax) require a signed BAA with the provider to be HIPAA-compliant. Sending PHI to an unverified fax number is among the most common — and easiest to avoid — disclosure violations OCR encounters.
🔟 HIPAA Breach Notification: What Dental Offices Must Do After an Incident
When an unsecured PHI exposure occurs — whether through a ransomware attack, a misdirected email, a stolen laptop, or an employee accessing records without authorisation — the Breach Notification Rule establishes a clear timeline and sequence of required actions.
Individual Notification: Affected patients must be notified without unreasonable delay and no later than 60 calendar days after discovery of the breach. Written notice is required, delivered by first-class mail or email if the patient has previously agreed to electronic communications.
OCR Notification: All breaches affecting 500 or more individuals must be reported to OCR within 60 days of discovery. Breaches affecting fewer than 500 individuals may be logged and reported to OCR annually — but must still be reported. Many dental practices incorrectly believe small incidents do not require OCR notification. They do.
Media Notification: If a breach affects 500 or more residents of a single state or jurisdiction, the dental practice must notify prominent media outlets serving that area — in addition to individual and OCR notification. This threshold is lower than many practices assume.
Business Associate Breaches: If a Business Associate (billing company, IT provider, cloud storage) discovers a breach involving your patients’ PHI, they must notify you within 60 days of discovery. You then own the notification obligation to patients and OCR. Ensure your BAAs include specific breach notification timelines and a requirement for immediate verbal notification followed by written confirmation.
VISTA Insight: Practices that have a documented incident response plan and a pre-prepared notification template consistently meet OCR timelines and avoid escalation to corrective action. Practices that improvise their response under regulatory deadline pressure typically generate additional documentation gaps that extend the investigation. Prepare the plan before you need it.
🚨 Experienced a Potential Breach?
Time is critical. VISTA InfoSec’s incident response team can step in immediately to contain the exposure, assess PHI involvement, and manage OCR notification strategy to minimise enforcement risk.
👉 Contact VISTA InfoSec Incident Response Now →
1️⃣1️⃣ HIPAA Compliance Checklist for Dental Offices
| Control Area | What It Involves | Why It Matters | Status |
| Risk Assessment | Document where patient data flows and identify gaps in systems and processes | Helps detect exposure points before they lead to incidents | Annual – Required |
| Access Controls | Use unique user IDs and strong password requirements | Prevents unauthorised access and shared accountability | Ongoing |
| Role-Based Access Control (RBAC) | Map staff access privileges to clinical vs. administrative roles | Ensures minimum necessary access and produces attributable audit logs | Implement |
| Secure Communications | Use encrypted email for referrals and data sharing | Protects patient records while in transit | Ongoing |
| HIPAA-Compliant Email / Fax Platform + BAA | Verify provider has signed BAA and supports encryption | Default Gmail/Outlook are not compliant without configuration | Verify |
| Staff Training | Conduct annual training on phishing awareness and secure workflows | Reduces human-error–driven breaches | Annual – Required |
| Training Documentation | Maintain signed acknowledgement records with date and content covered | OCR requires evidence of training, not just a training programme | Document |
| Vendor Management | Verify BAAs for IT, billing, and cloud providers | Ensures third parties meet regulatory obligations | Annual Review |
| Vendor BAA Registry | Maintain a log of all BAAs with execution dates and renewal schedule | Absence of a BAA is a standalone HIPAA violation regardless of breach | Maintain |
| Notice of Privacy Practices (NPP) | Post in office and provide to new patients at first visit | Required under the Privacy Rule – absence is a common OCR finding | Post & Distribute |
| Breach Notification Procedures | Document response steps for incidents of all sizes | Undocumented response process extends OCR investigations significantly | Document |
| Audit Log Review | Review system access logs on a scheduled basis (monthly recommended) | Detects insider threats and anomalous access patterns before escalation | Monthly |
| Workforce Sanctions Policy | Define consequences for HIPAA violations by staff | Required under HIPAA – demonstrates enforcement intent to OCR | Document |
| Contingency & Disaster Recovery Plan | Document backup procedures and recovery steps for data loss events | Required under the Security Rule – critical for ransomware response | Document & Test |
| Practice Management Software BAA | Verify BAA exists with Dentrix, Eaglesoft, Open Dental, or equivalent | Software vendors handling ePHI must have a signed BAA | Verify |
1️⃣2️⃣ What to Do When OCR Contacts Your Practice
An OCR contact letter is not an accusation — but it is a signal that your response quality over the next 30–60 days will determine whether the matter closes administratively or escalates to a formal corrective action plan. The majority of dental practices that receive OCR inquiry letters have never interacted with a federal regulator before. Here is what to do immediately.
Do not respond without legal and compliance counsel. Your initial response sets the evidentiary record. An imprecise or over-broad admission in a first response can expand the scope of investigation significantly. Retain a HIPAA compliance consultant or healthcare attorney before sending any written response to OCR.
Gather documentation systematically. OCR will request: your most recent risk assessment, your written HIPAA policies and procedures, training records for all workforce members, your BAA registry, relevant access logs and audit trails, and the incident timeline if the inquiry follows a reported breach. Organise these into a structured evidence package before the response deadline.
Respond within the stated deadline. Failing to respond by OCR’s stated deadline — typically 30 days for initial information requests — can itself result in escalation. If you need additional time to gather documentation, request an extension in writing before the deadline passes, not after.
Do not destroy or alter records. From the moment you receive OCR correspondence, preserve all documentation in its current state. Do not update or backdate policies, delete access logs, or alter incident records. Obstruction is treated as a separate and serious violation.
| VISTA InfoSec Support: VISTA InfoSec’s incident response team has managed formal OCR investigations on behalf of healthcare clients across multiple jurisdictions. Our structured evidence approach reduced follow-up requests and shortened investigation timelines — and in each case, the practice’s documentation quality was the determining factor in the outcome. Contact us before you respond. |
1️⃣3️⃣ Conclusion
Most dental HIPAA violations do not start with a cyberattack. They start with a shared login that nobody questioned, a paper schedule left visible at the front desk, or a billing vendor that never signed a Business Associate Agreement. By the time OCR opens an investigation, the exposure has often been there for months — sometimes years. The practices that survive regulatory scrutiny are not the ones with perfect policies. They are the ones who can show exactly how their policies map to how the practice actually operates, every day.
✅ If OCR emailed your practice tomorrow morning, would you open policies—or pull proof?
This is your moment to step back and ask a simple question: If an OCR inquiry starts tomorrow, could you clearly show how patient data is protected across people, systems, and vendors?
If the answer isn’t an immediate yes, the next step isn’t more policy language—it’s visibility. Map where PHI actually flows. Assign clear ownership. Test your safeguards against how your office really operates, not how it’s supposed to operate on paper. Compliance becomes defensible only when written HIPAA intent matches how dental data is actually accessed, stored, and shared.
Don’t let growth and transformation outpace your HIPAA security posture.
👉 Engage VISTA InfoSec to secure compliance across your extended healthcare ecosystem—today and at scale.
📺 Explore VISTA InfoSec’s YouTube Channel to learn more.
👉 HIPAA Audit, Compliance & Consultancy Services at VISTA InfoSec
✅ HIPAA @ VISTA InfoSec
1️⃣4️⃣ Frequently Asked Questions
Q: Does HIPAA apply to all dental offices
A: Yes. Any dental office that transmits health information electronically — including electronic insurance claims — is a Covered Entity under HIPAA and is subject to the full Privacy, Security, and Breach Notification Rules. Solo practitioners are not exempt.
Q: What counts as PHI in a dental office
A: Any information that identifies a patient and relates to their health, treatment, or payment is PHI. This includes dental charts, X-rays, intraoral images, treatment plans, billing records, appointment schedules, insurance IDs, contact details, and SSNs. Both digital and paper records are in scope
Q: What are the HIPAA fine amounts for dental offices?
A: HIPAA civil monetary penalties range from $100 to $50,000 per violation, with annual caps of up to $1.9 million for the most serious (wilful neglect) cases. Fines apply per violation category per year — so multiple simultaneous failures can compound rapidly. OCR can also mandate corrective action plans, which require 1–3 years of monitored compliance at the practice’s expense.
Q: How often must dental staff complete HIPAA training
A: HIPAA requires workforce training upon hire and whenever material changes to policies occur. Annual refresher training is an industry standard and is expected by OCR during investigations. Training must be documented — OCR requests training records by name, date, and content. Verbal training with no record is treated the same as no training at all.
Q: What should a dental office do immediately after a potential breach?
A: Follow your breach notification plan: (1) contain the exposure, (2) assess whether PHI was involved, (3) document the discovery date, (4) notify affected individuals within 60 days, (5) notify OCR — within 60 days for breaches affecting 500+ individuals; annually for smaller breaches. Contact a HIPAA compliance consultant before drafting external notifications.
Appendix: Key Terms Glossary
- BAA (Business Associate Agreement): A mandatory contract between a dental office and a vendor (e.g., IT provider, cloud storage) that ensures the vendor will protect PHI according to HIPAA standards.
- CE (Covered Entity): Any healthcare provider, including dentists, who transmit health information in electronic form.
- ePHI (Electronic Protected Health Information): Any PHI created, stored, or transmitted electronically (e.g., digital X-rays or practice management software).
- HHS (U.S. Dept. of Health & Human Services): The federal department responsible for protecting the health of all Americans.
- MFA (Multi-Factor Authentication): A security process requiring two or more pieces of evidence to verify identity (e.g., a password plus a code sent to a phone).
- OCR (Office for Civil Rights): The sub-agency within HHS that enforces HIPAA rules through audits and investigations.
- PHI (Protected Health Information): Any information—physical or digital—that can identify a patient and relates to their health or payment.
- TPO (Treatment, Payment, and Operations): The primary reasons a dental office is allowed to disclose PHI without a specific patient authorization.
- RBAC (Role-Based Access Control): A method of restricting system access so that staff can only view or modify records relevant to their specific job function. Required under HIPAA’s minimum necessary standard.
- PACS (Picture Archiving and Communication System): The imaging server system used by most dental offices to store digital X-rays and intraoral images. A primary target for ransomware actors due to legacy software and weak network segmentation.
- Risk Register: A documented log of identified HIPAA risks, their likelihood and impact scores, and the status of remediation actions. The core deliverable OCR expects from a completed risk assessment.
- Minimum Necessary Standard: The HIPAA principle that staff and vendors should only access the minimum amount of PHI necessary to perform their specific function. Violations of this standard are among the most common findings in OCR investigations.
- Corrective Action Plan (CAP): A formal agreement between OCR and a covered entity following an investigation. CAPs typically require 1–3 years of monitored compliance, policy rewrites, and staff retraining at the practice’s expense.
Narendra Sahoo (PCI QPA, PCI QSA, PCI SSF ASSESSOR, CISSP, CISA, CRISC, 27001 LA) is the Founder and Director of VISTA InfoSec, a global Information Security Consulting firm, based in the US, Singapore & India. Mr. Sahoo holds more than 25 years of experience in the IT Industry, with expertise in Information Risk Consulting, Assessment, & Compliance services. VISTA InfoSec specializes in Information Security audit, consulting and certification services which include GDPR, HIPAA, CCPA, NESA, MAS-TRM, PCI DSS Compliance & Audit, PCI PIN, SOC2 Compliance & Audit, PDPA, PDPB to name a few. The company has for years (since 2004) worked with organizations across the globe to address the Regulatory and Information Security challenges in their industry. VISTA InfoSec has been instrumental in helping top multinational companies achieve compliance and secure their IT infrastructure.




